DDoS or Distributed Denial of Services, also known as denial of service attack, is a type of cyber attack (if you want to know more check out our article on Cyber Attacks) where the hacker (or attacker/attacker) tries to overload a server, a piece of network equipment such as router, switch, BRAS/BNG, firewall, a computer or a network so that services or their use become unavailable.
Distributed denial of service attacks, DDoS, do not aim to steal information from victims, but rather to bring down or render inoperative a network or a service (understand a service as a web server, a database, a bank application). DDoS can also serve as a “smokescreen” to hide other attacks that may occur at the same time, and these are for stealing information.
Unlike DoS, where only one computer or host is used in the attack, DDoS uses thousands and even millions of computers and devices to attack its victims
Plus why would anyone do that?!
Within the various reasons we have for a DDoS attack, over time the most common ones are:
- Competitors in the same segment
- Money extortion
- Personal problems between directors or employees
- Denigrating the image of another company
- Distraction for other attacks
- Ideological or Political Beliefs
- Fun for some hackers
- Fame or Status for hackers
- For some hackers it is a business to sell DDoS attacks
- And many other reasons that bad-intentioned people may have
But now in 2021 do I need to worry about DDoS?
The answer to this is: YOU NEED TO CARE, here below is some news from around the world:
And it is not only big people that take DDoS attacks, like a carrier or a big service company, over the years we have seen many small companies taking DDoS attacks with high volume and many different forms of attack.
A second factor for you to worry about is prices to generate a DDoS attack, some sites have “DDoS starting at 5 euros”, so if someone has a little bit of money they don’t have to be a hacker to generate a DDoS against someone.
So if you have a network it is important to worry about DDoS.
But how does a DDoS attack work?
Here in this article I will explain how it works in a very basic way, if you want to know a little more in depth check out our more detailed article How a DDoS Attack Works.
DDoS attacks usually happen via botnet or zombie networks controlled by hackers. These networks can have millions of devices controlled by the hacker, who can simply send a command to all these devices to start sending packets to the victim, thus generating the DDoS Attack. Various devices are prone to being zombies in a botnet such as: computers with viruses, security cameras with vulnerabilities, home routers (or CPE) with vulnerabilities, IoT equipment and even your smart refrigerator can be a zombie in a botnet.
The image below demonstrates a little better how a DDoS works:
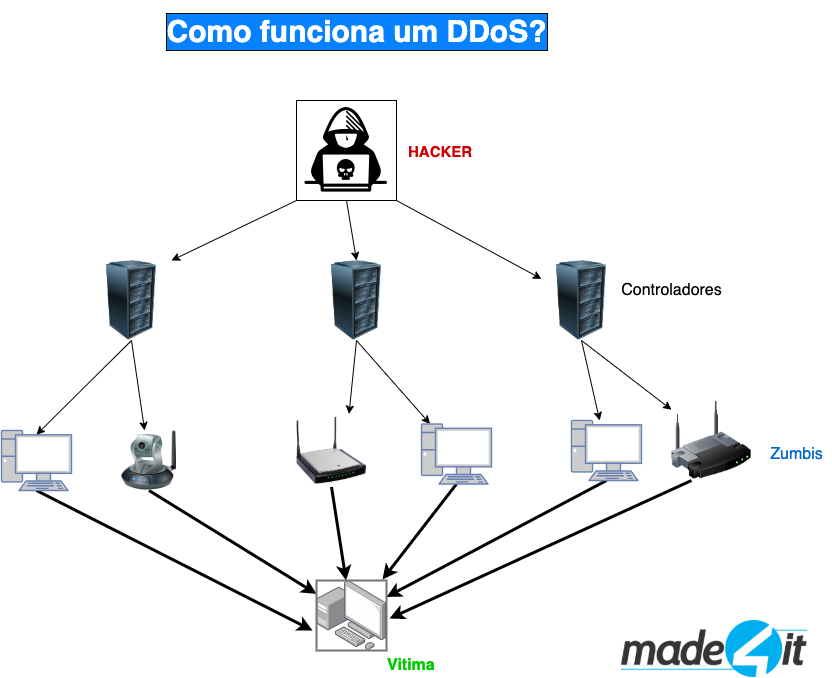
The hacker uses remote servers, which in the design are called controllers, where he uses these servers to send commands to the zombies, which can be millions of infected devices with security flaws, to send packets (or data) to the victim of the attack, thus generating millions of packets and a huge traffic creating DDoS and probably overloading the servers and the network and affecting the services.
Some attacks have very large amplifications, such as NTP (123/UDP) that can amplify up to 556 times, SSDP (1900/UDP) that can be amplified 30 times, or Chargen (19/UDP) that can be amplified up to 358 times. On the cert.br website you can check out some more protocols that can be amplified by botnets: https://www.cert.br/docs/whitepapers/ddos/
And how can I protect myself?
There is no magic formula and no TOTAL solution against DDoS (there is: leave your computer turned off lol) but there are some measures you need to adopt to decrease the chances that someone will attack you. I will point out a few here:
1 – Do your homework
If your network is all open, with all ports open to everything on the Internet you have a big problem. But as measures to lessen the attacks you can:
– Use firewall to control access to equipment management
– Turn off what you don’t use in your backbone and network equipment
– In IPv6 you also need to protect yourself
– Block Spoofing with uRPF or firewall
– Validate the configuration of your servers and network equipment
– Take care of your Customers’ equipment such as: CPE/Routers and smaller last-mile equipment. Blocking access to their management is a good way
2 – Create your protection structure
Unfortunately attacks will occur even if you do your homework, so preparing for the “bad” day is key. Creating a protective framework is important to note several points and anticipate what attacks will change.
But how to protect yourself?
We will cover 2 ways in this article:
1) Blackhole BGP
Through RTBH (Remote Triggered Black Hole) you can advertise via BGP a route that will go to the Blackhole. With it, packets bound for that IP will be dropped, and through BGP you can tell your Upstreams to do the same until the IP stops working for the entire Internet.
One of the limiting factors is that the advertised IP in the blackhole stops working and a second limiting factor is the maximum amount of IPs in the blackhole, most carriers limit the BGP session to a few routes, if you advertise more than the exceeded amount the BGP session will be down and your traffic will use other paths.
If your attack changes and starts attacking multiple IP’s in your network you will need to use the Scrubbing Center/Mitigation to clean up the attacks.
2) Scrubbing Center/Mitigation Unlike Blackhole.
The Scrubbing Center or Mitigation, some still call it Cloud AntiDDoS, Protected Traffic and some more variants, are the traffic scrubbing centers. When you receive an attack instead of sending a Blackhole as mentioned above you can send your traffic to the Scrubbing center which will clean up the attack, literally like separating the “chaff from the wheat”, the chaff being attack packets and the wheat being clean traffic. Usually Scrubbing Centers are purchased by Clean-Pipe or clean traffic capacity.
Scrubbing centers can be hired during attacks, but since we are talking about planning it is very important to evaluate characteristics, points of presence, and latency.
It is normal when traffic is in mitigation that your latency goes up or you have problems accessing some sites.
Most importantly, you need to automate this!
Both blackhole and scrubbing center will not trigger by themselves and you need to intervene manually, but as human beings, network administrators will not be logged in 100% of the time and looking at graphs or network traffic.
To make this not a problem for you, there are solutions where you can automate the detection of attacks and also the necessary actions like Blackhole and sending the traffic to the Scrubbing Center, and the best of them is Made4Flow.
With it, you can configure it to identify attacks and already take necessary actions, and you can even be warned that there was an attack and our solution already protects you, all in less than 2 minutes!
If you are under attack or suffering from attack contact us, we can help you!
In upcoming posts we will have more details about DDoS, how they work in practice, how to configure Blackhole BGP sessions, for a scrubbing center and much more!
If you want to know a little more about attacks too, we did a live broadcast almost 2 hours long giving many tips and showing how attacks work, click on the link to see it!
And also follow us on social networks to learn more about Made4it and Made4Flow