In recent months, our technical team has seen an alarming increase in DDoS attacks of the Carpet bombing type, characterized by intense traffic spikes generally directed at all IP addresses belonging to the ASN. These attacks have negatively impacted network connectivity, presenting an additional challenge in evading detection by many conventional DDoS security systems.
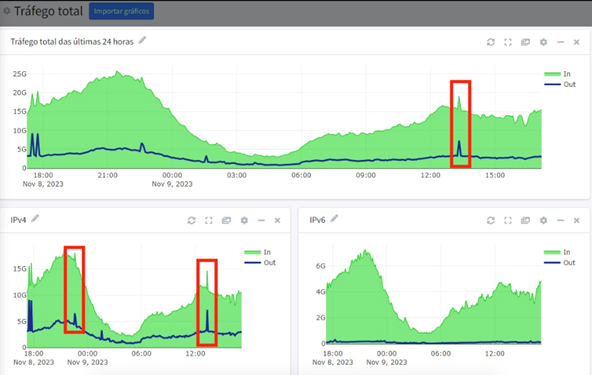
Unlike traditional attacks, which focus on a single IP address, these latest attacks show greater sophistication. They send smaller volumes of traffic distributed among several IP addresses, making identifying patterns and distinguishing between legitimate traffic and DDoS attacks a much more complex task.
In response to this evolution in cybercriminal tactics, Made4Flow‘s AntiDDoS development team has taken proactive measures. We recently implemented a series of new decoders to strengthen our detection system. This improvement aims to give greater precision and reliability to our anomaly detection and analysis tool, significantly improving our ability to identify and analyze anomalies. neutralize more sophisticated DDoS attacksby taking automated actions that have been previously configured in our tool, such as BGP prefix announcement for mitigation or Clean Pipe (Scrubing center), as well as reports of the identified attack.
In this article, we’ll explore the details of these new Decoders, developed on the basis of extensive Made4Flow analysis and packet captures. These implementations aim to improve the resilience of AntiDDoS, providing a more efficient defense against the complexities of contemporary DDoS attacks.
New Decoders from AntiDDoS Made4Flow:
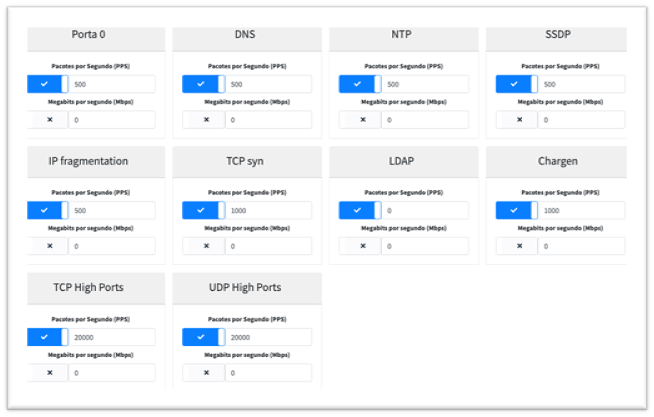
– Port 0: Allows the identification of DDoS attacks that use port ZERO in the UDP protocol in the IP packet, either as source or destination, as this tactic is often used in DDoS amplification attacks.
– DNS: A feature of DDoS attacks are packets received from DNS Servers or Hosts responding to DNS requests. These attacks are known as DNS amplification and involve zombie machines (infected machines), the Server or Assets answering the DNS request and the target.
– NTP: Another widely used tactic is attacks using NTP servers. Like DNS-based attacks, these attacks are known as NTP amplification, taking advantage of servers or hosts that respond to NTP to direct the attack at their target. Although it is common for devices connected to the network to make NTP queries to keep the date and time up to date, it is possible to strengthen the identification of DDoS attacks by setting a common traffic limit via a decoder.
– SSDP: The Simple Service Discovery Protocol (SSDP) can be exploited to send large volumes of packets to the Target, abusing device discovery services to amplify the attack and affect the Target’s connectivity.
– IP Fragmentation: Packet fragmentation can occur when a device is unable to send all the necessary information in a single packet. The big problem is that firewall blocks may not be as efficient and large DNS request responses may use fragmented packets. An excess of these packets can affect the network and consume too many resources from network devices. With this decoder, we can set a limit and make detection more precise.
– TCP Syn: This decoder plays a key role in detecting attacks known as Syn Flood, which consists of consuming resources from servers or device services, leaving it unavailable for use. By setting the correct threshold, we can implement effective preventive measures, preventing this type of attack from occurring and taking actions that result in immediate mitigation.
– LDAP: The LDAP Decoder plays an important role in identifying DDoS attacks that exploit servers with active LDAP to perform reflections, thus amplifying malicious traffic.
– Chargen: Despite being an older protocol, it is used in some line printers and can be exploited by an attacker. Having a defined limit for this type of traffic is also important.
– TCP and UDP High Ports: In addition to the protocols mentioned above, we have observed in several DDoS attack reports the use of high ports, higher than port 1024, with the TCP and UDP transport protocols. It is therefore important to define limits for these 2 protocols, making it more assertive to detect attacks that use high ports.
The inclusion of new Decoders makes DDoS attack detection more efficient, with a variety of protocols, protecting against different types of DDoS attacks, minimizing false positives and enabling more accurate identification of real threats.


