Blackhole or in literal translation “black hole” is a technique that discards packets destined for an IP or range of IP’s at the edge routers (BGP) of an Internet Provider. Once a DDoS attack is detected, Blackhole can be used to drop all traffic destined to the attacked IP or IP range, thus protecting the network from being overloaded or stopped by the volume of DDoS traffic
RTBH or Remote Triggered Blackhole is the technique that through BGP the traffic destined to the attacked IP can be easily dropped at the Backbone or BGP layer, thus preventing the entire network from stopping or suffering degradation because of the DDoS Attack.
To make the explanation easier let’s give an example: The provider XPTO has the prefix 200.200.200.0/24 associated with its ASN123456, and within this provider there is a company Bubble that suffered a DDoS attack, so that the provider’s network XPTO not stop completely, they add the configuration of blackhole for this company Bubble, thus protecting your infrastructure and leaving only the company Bubble without services
What are the pros and cons?
Pros:
- Efficient against DDoS attacks
- Its deployment is very simple and fast
- Support for all vendors (equipment brands)
- Widely deployed in Operators of all sizes
Cons:
- The blackhole IP stops working completely
- In attacks directed to several IP’s it can generate more problems than solutions
How does Blackhole work in practice?
As soon as the attack is detected, through a Netflow analysis, Made4Flow is an example of Netflow analysis software or via a port mirror and it is determined which is the destination IP of the DDoS attack it is possible to configure the router to send the route to the Blackhole or more specifically to Null0 (Cisco/Huawei routers) or Discard (Juniper) or Blackhole (Mikrotik), literally throwing that route to the “black hole” thus discarding the traffic destined to that IP.
In the world of BGP it is possible to send this Blackhole route to your carrier so that it can discard the packets within its network and also send it to all the carriers so that the whole world knows that this IP no longer works. We will show later how Blackhole works in the BGP world.
How to configure the Blackhole?
After determining the attacked IP the Router operator accesses the equipment, configures a static route with the Attack destination IP being its next-hop (or gateway) as Null0 or Blackhole
An example of configuration on Huawei Routers is the following syntax:
[~rt-huawei-ne40]ip route-static 200.200.200.200 32 NULL 0
Explaining the command: Every packet going to IP 200.200.200.200 will be sent to Null0 (Blackhole) and all its traffic discarded.
You still need to advertise via BGP this blackhole route so that your carriers receive and also discard the traffic to this attacked IP. For clarity, we have the image below demonstrating the entire Blackhole announcement process
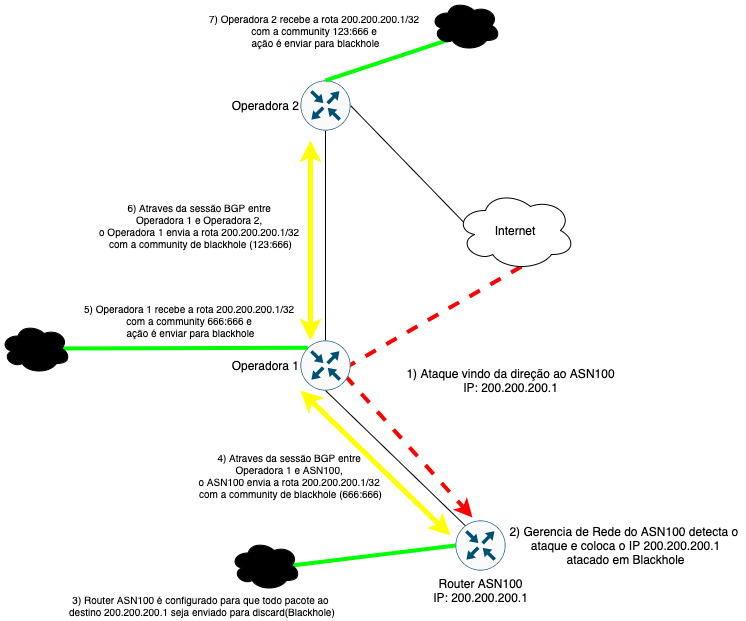
In the following articles we will show you how to configure Blackhole on Huawei, Cisco, Juniper, and Mikrotik routers.
If you have any questions, please contact us via Social Networking or WhatsApp!
Until the next articles!


