Now that you know what a BGP Blackhole is (if you still don’t know, check out our article on RTBH – Blackhole). Now it’s time to configure it and be able to protect yourself from DDoS attacks.
To summarize the Blackhole, it is a technique of sending a route to the “black hole” or simply making the router discard packets directed to that IP. With Blackhole you can also announce these attacked IPs to your suppliers/upstreams and thus stop the attacks.
Now that I know what it is, now comes the question, how to blackhole my router? In today’s article we will show you how to configure Blackhole on Cisco routers
To do the Blackhole manually we have some steps that are:
- Identify the attacked IP;
- Create the route to blackhole;
- Advertise this blackhole route via BGP to your carriers/upstreams.
You can automate all of this with Made4Flow, already closing a direct session and not having to do manual work.
Let’s go to the settings then
1 – Identify the attacked IP
You can do this through Netflow analysis, as in Made4Flow, through the graphs and identify through the Raw Data Report, which IP has the most traffic and possibly being the victim of the attack.
Within Made4Flow, access, for example, the Interface Graph by Application, then, by clicking on the most used port, you can identify which IP is being attacked, or through Made4Flow, simply by accessing the Anti-DDoS module -> Active Anomalies.
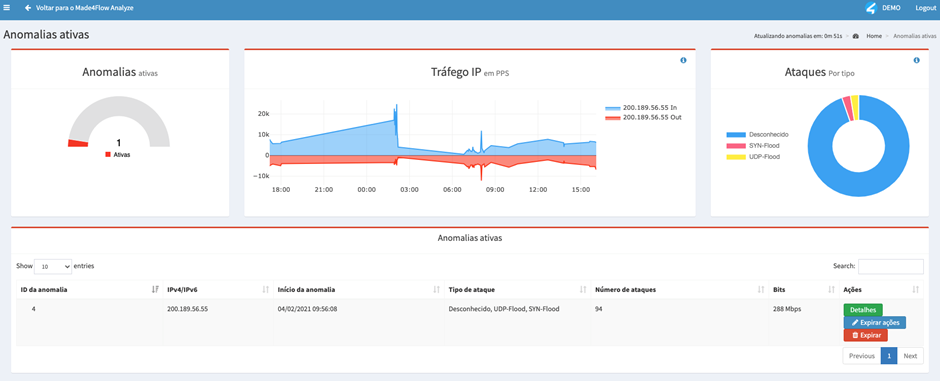
The attacked IP was: 200.189.56.55 (Example)
2) Create a route to Blackhole or Null0
After identifying the attacked IP via Made4Flow, now it’s time to create the route on your Cisco Router to effectively throw the IP to Blackhole or Null0.
Let’s assume that the attacked IP is 200.200.200.1, let’s create the route as follows
Commands applied:
enable
configure terminal
ip route 200.200.200.1 255.255.255.255 Null0
After applying the route pointing to Null0 this IP will STOP WORKING!
You can check the route using the show command:
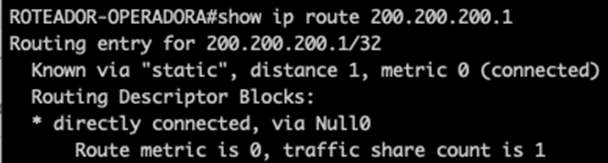
If the route is showing as Null0 then you are already sending it to Blackhole.
3 – Advertise the IP in blackhole via BGP to your operators/upstreams
After identifying and blackhole the route, you need to advertise via BGP to your carriers/upstreams.
Note: Before setting up, it is always recommended to talk to your Operator/Upstream to find out which Blackhole BGP community is.
The BGP session with your carrier needs to be established.
For this we have a few steps:
Configure your Carrier/Upstream Blackhole Community
To configure the blackhole community to be used later, we need to run the following command:
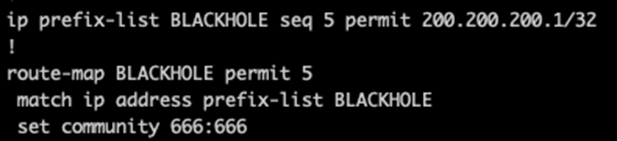
Commands:
ip prefix-list BLACKHOLE permit 200.200.200.1/32
route-map BLACKHOLE permit
match ip address prefix-list BLACKHOLE
set community 666:666
set community 666:666
In case it is necessary to add more communities, apply the same command changing the community name and number.
Tip: Talk to your operator to find out which BGP blackhole community they use.
Announce the attacked IP with the BlackHole community for Upstream
To carry out the advertisement of the attacked IP with the blackhole community, it is necessary to carry out the following steps;
Enter the Cisco router’s BGP configuration
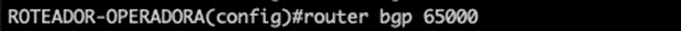
After that, we announce the attacked IP to our Upstream, using the command below;

Commands:
router bgp 65000
neighbor 192.168.100.1 as 64700
neighbor 192.168.100.1 route-map BLACKHOLE out
Automating with Made4Flow
With Made4Flow, it is possible to automate the blackhole announcement process of attacked IPs.
For that we need:
- Configure the BGP session between the Edge Router and Made4Flow;
To configure the BGP session between the Router and Made4Flow, you need to create a route-map and then the BGP session.
To configure the route-map:
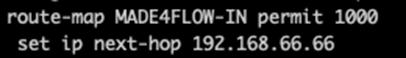
Comando: route-map MADE4FLOW-IN permit 1000
set ip nex-hop 192.168.66.66
In this case it is necessary to add Next-hop manually on the router.
Within Made4Flow, you can already advertise with the BGP community and the correct Next-hop if you prefer.
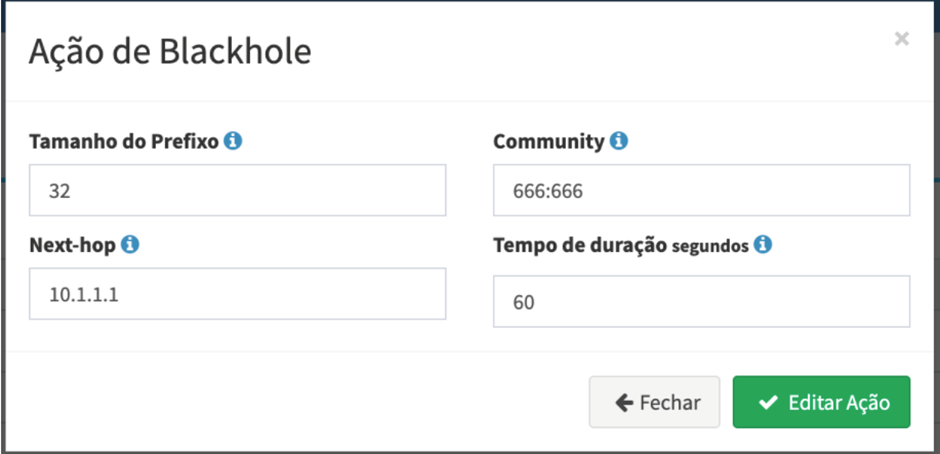
Configure Made4Flow to send via Actions
Within the Anti-DDoS Module, you can access the menu: Actions and Responses and configure the response to send the Blackhole with the correct BGP community:
Configure the Router to Send to Carriers
To configure to send to operators/upstreams you need to configure so that the BGP community is identified in the outbound Route-map match.
For this we need to configure an ip community-filter
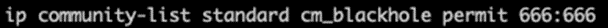
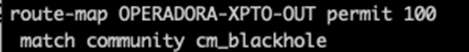
The next step is to configure the Route-map of your operator/upstream, as in sending the blackhole, but now matching the community in the match, as in our configuration:
Check if you receive from Made4Flow
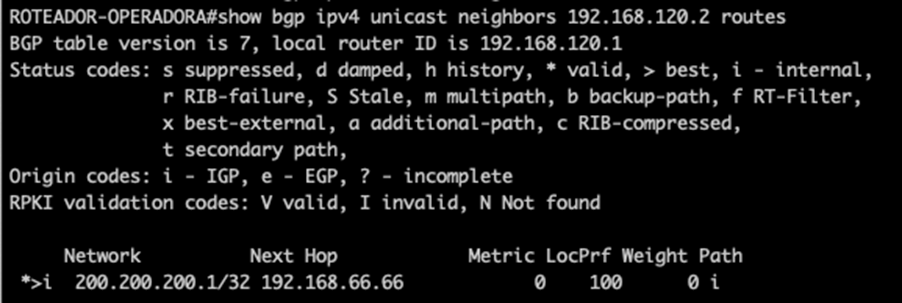
Command:
show bgp ipv4 unicast neighbors 192.168.120.2 routes
And if you are sending to the operator:
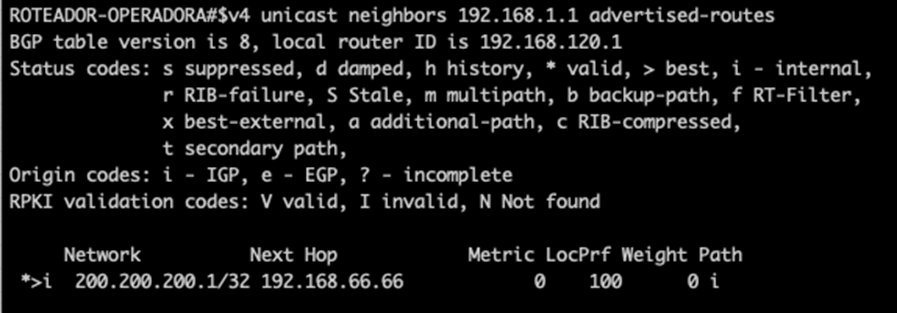
Command:
show bgp ipv4 unicast neighbors 192.168.1.1 advertised-routes
Having made these settings, the automation of Made4Flow is ready. Upon receiving an attack, Made4Flow can now send this route to Blackhole.
We have other content on how to configure Blackhole that you can find on our blog and any questions you still have, please contact our team of experts
Leonardo Nascimento | Made4it consultant


