Now that you know what a BGP blackhole is (if you still know, check out our article on RTBH – Blackhole). Now it’s time to configure it in Mikrotike to be able to protect yourself from DDoS attacks.
To summarize the Blackhole, it is a technique of sending a route to the “black hole” or simply making the router discard packets directed to that IP.
Now that I know what, now comes the question how to blackhole my router? In today’s article we will show how to configure Blackhole in Mikrotik Routers running RouterOS.
To do the Blackhole manually we have some steps that are:
- Identify the attacked IP
- Create route to blackhole
- Advertise this blackhole route via BGP to your carriers/upstreams
You can automate all of this with Made4Flow, already closing a direct session and not having to do manual work.
If you want to know how to automate everything with Made4Flow, check out our next article.
So let’s go to the settings:
1 – Identify the attacked IP
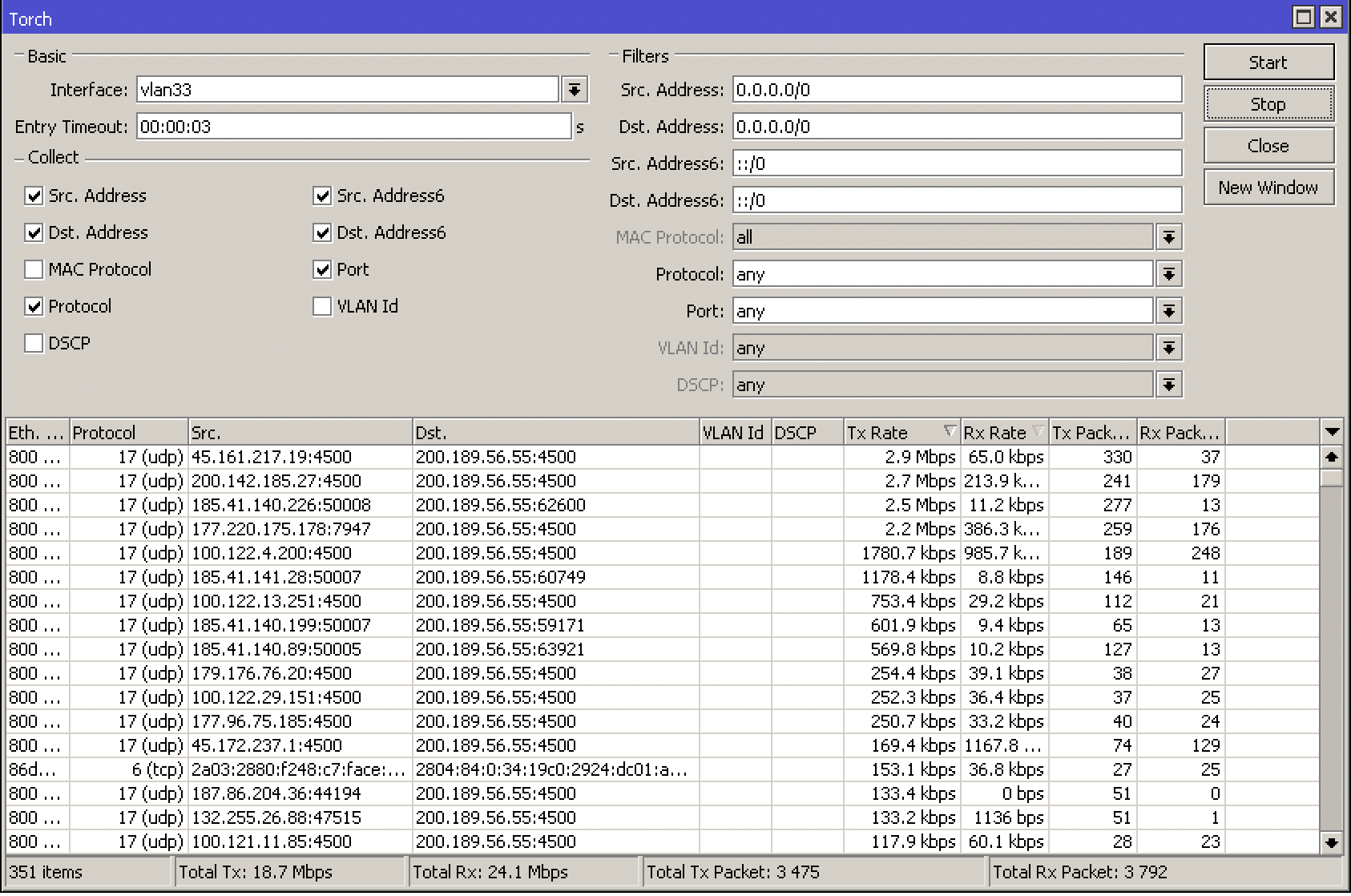
You can use some of Mikrotik’s own tools like Torch or use a Netflow Software that has a DDoS attack sensor like Made4Flow
Via Torch, go to Tools -> Torch and choose the interface where you are being attacked
Or in Made4Flow in a simple way by accessing Anti-DDoS -> Active Anomalies
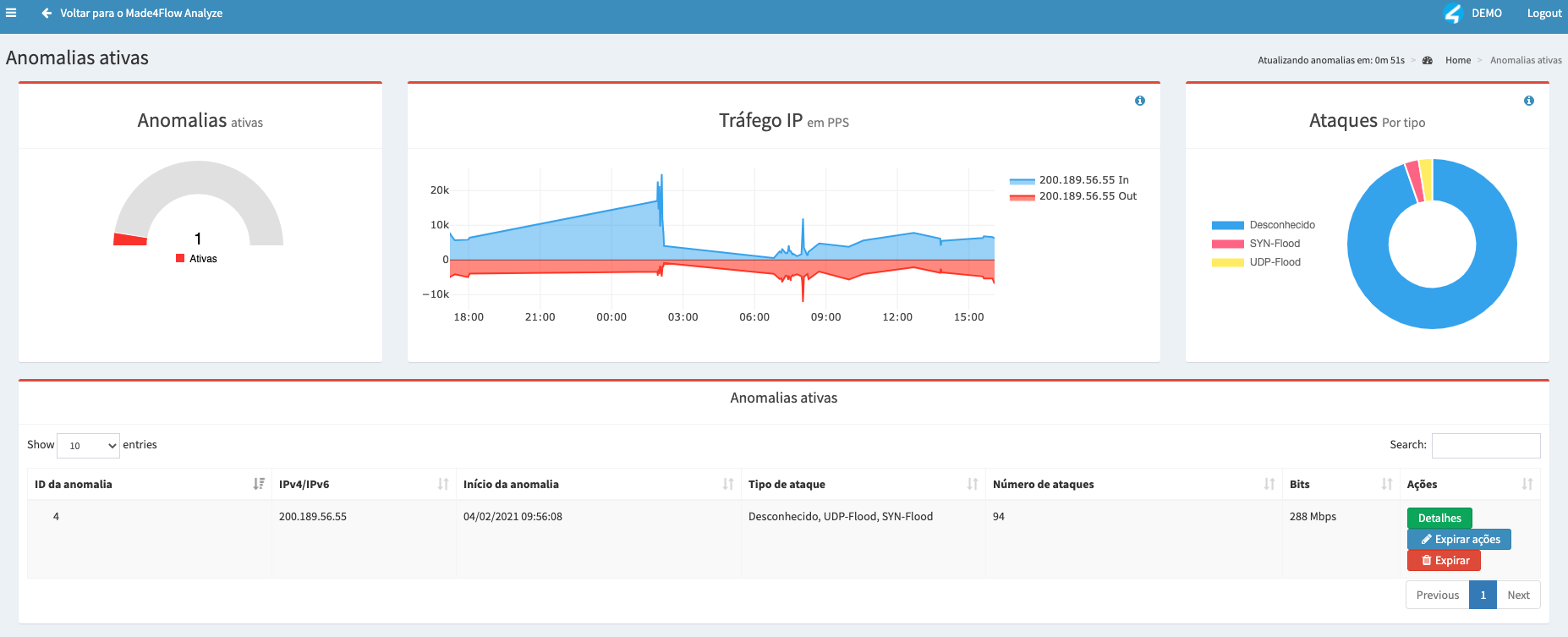
The attacked IP was: 200.189.56.55 (Example)
2) Create a route to blackhole
After identifying the IP attacked via Torch or via Made4Flow, now it’s time to create the route on your Router
For that go to IP -> Routes and add a new Route
Let’s assume that the attacked IP is 200.200.200.1, let’s create the route as follows
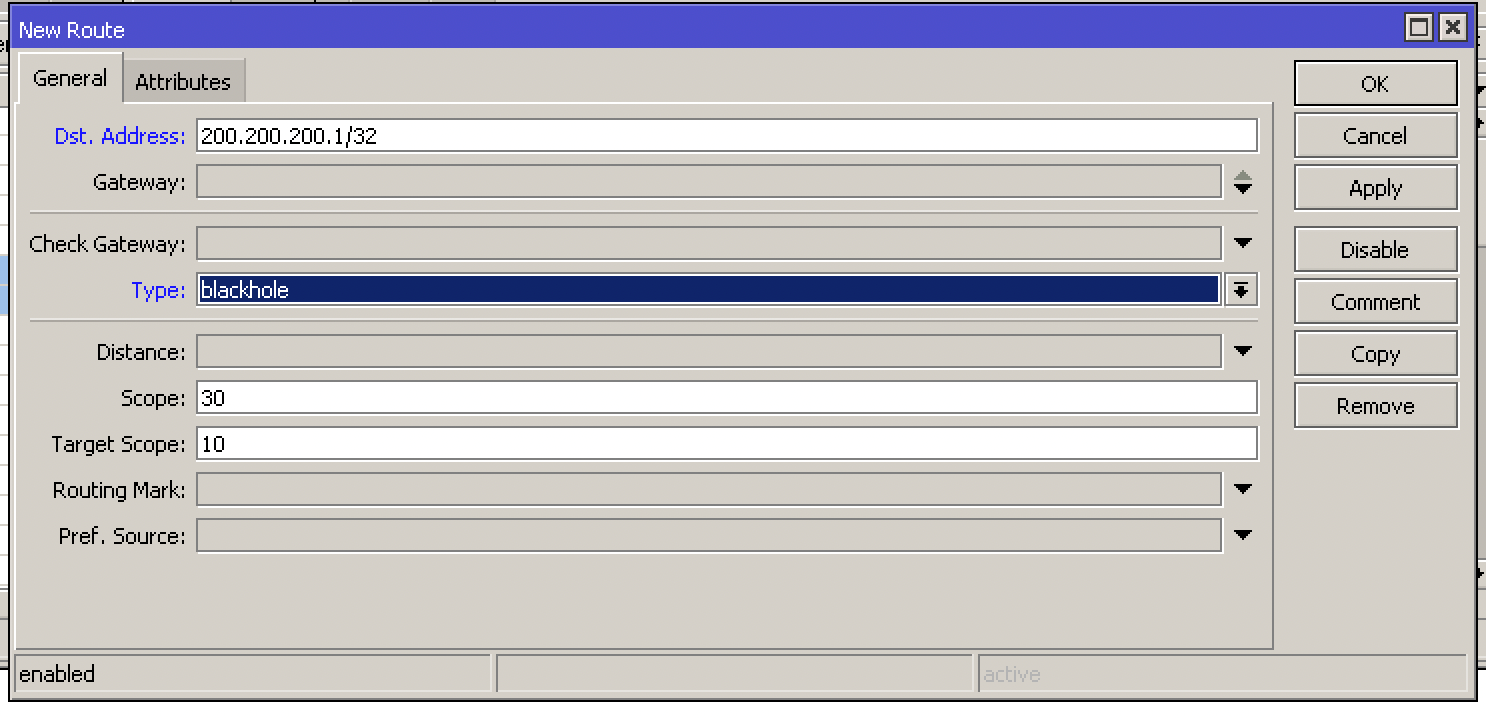
Add the Dst-address as 200.200.200.1/32, to identify that it is only the specific IP and the Blackhole type
Or via terminal with the following command:
/ip route
add distance=1 dst-address=200.200.200.1/32 type=blackhole
After applying the route in blackhole this IP will STOP WORKING!
3 – Advertise this blackhole route via BGP to your carriers/upstreams
After identifying and blackhole the route you need to advertise via BGP to your operators/upstreams.
For this we have a few steps:
- Create the Route for BGP
To do this go to Routing -> BGP -> Networks and add the route that is in blackhole
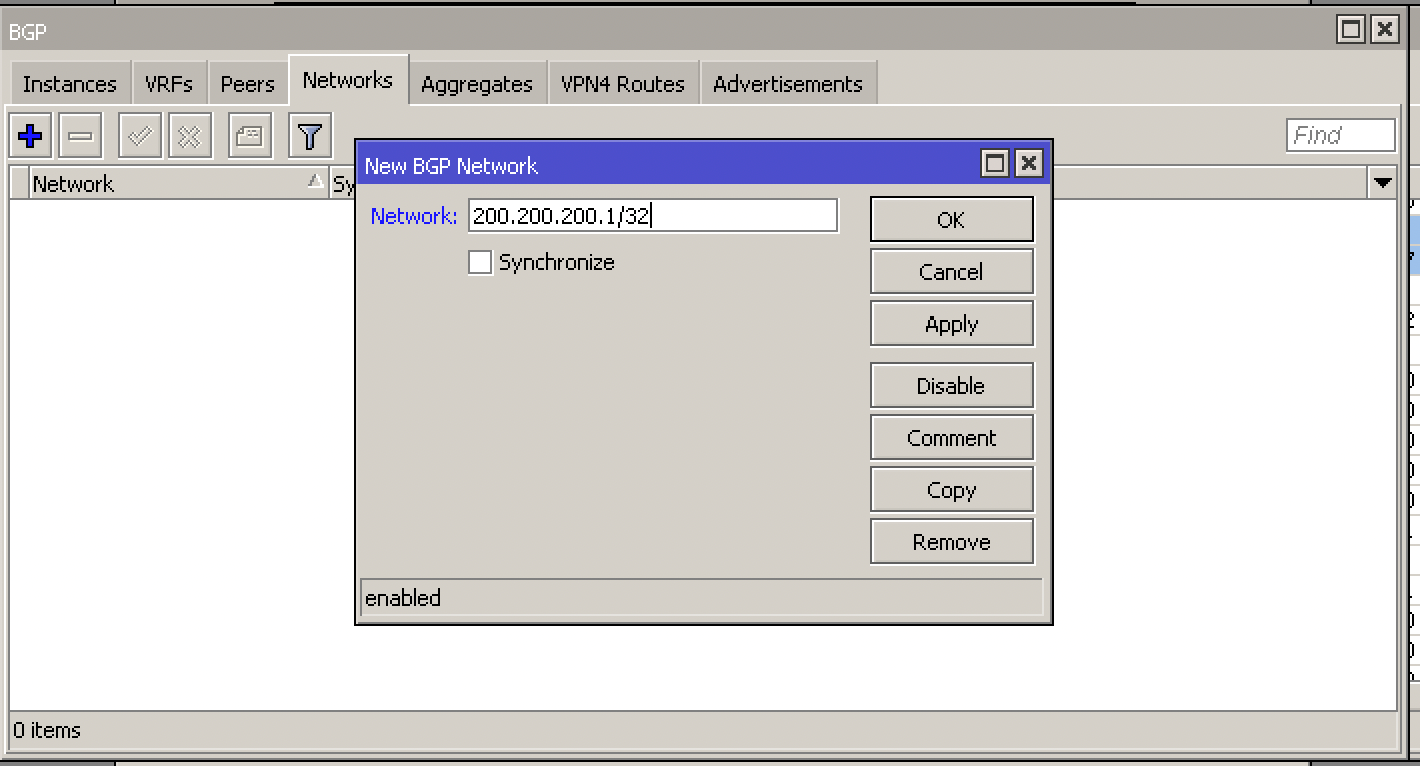
In our example the attacked IP was: 200.200.200.1/32
Or via command:
/routing bgp network
add network=200.200.200.1/32 synchronize=no
- Configure your Route-Map or Filters to send the advertisement
Enter Routing -> Filters and add the new Filter. In our example, the Filter of our operator XPTO has the name TRANSITO-XPTO-OUT and we are going to add it to send our blackhole route:
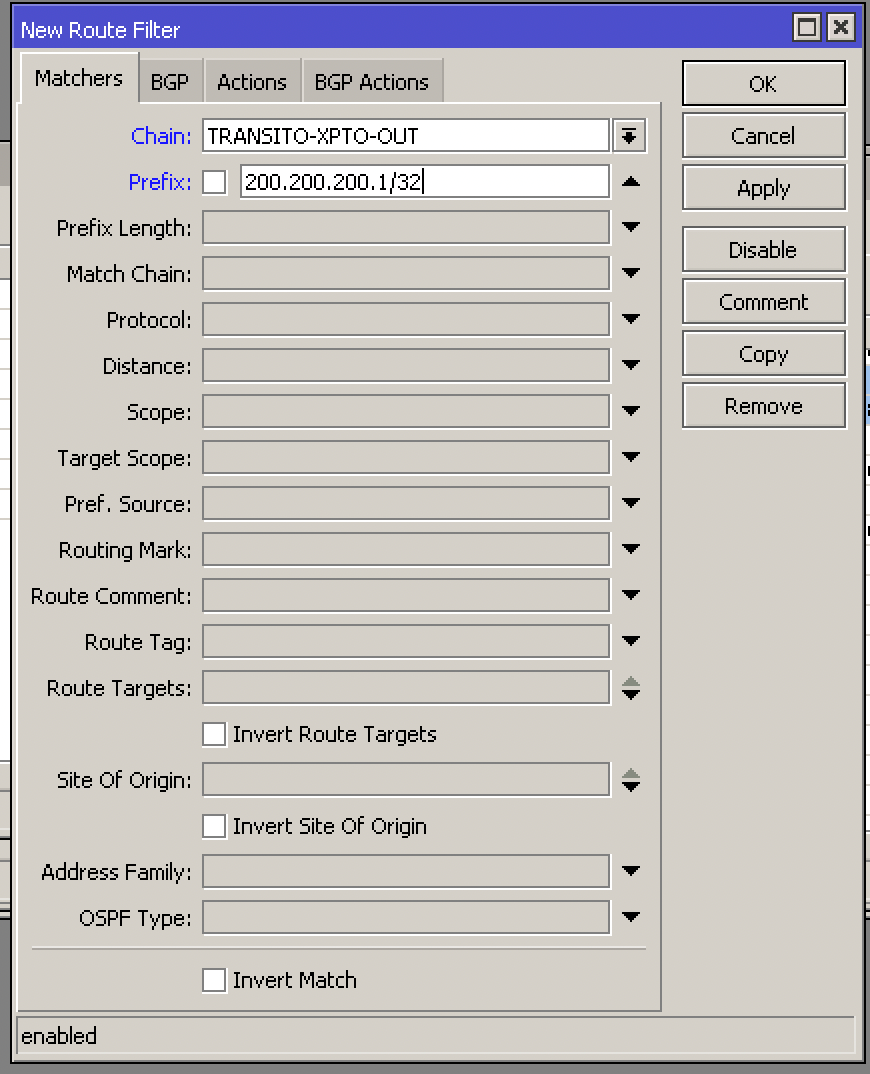
Add the IP attacked with the mask /32 in Prefix
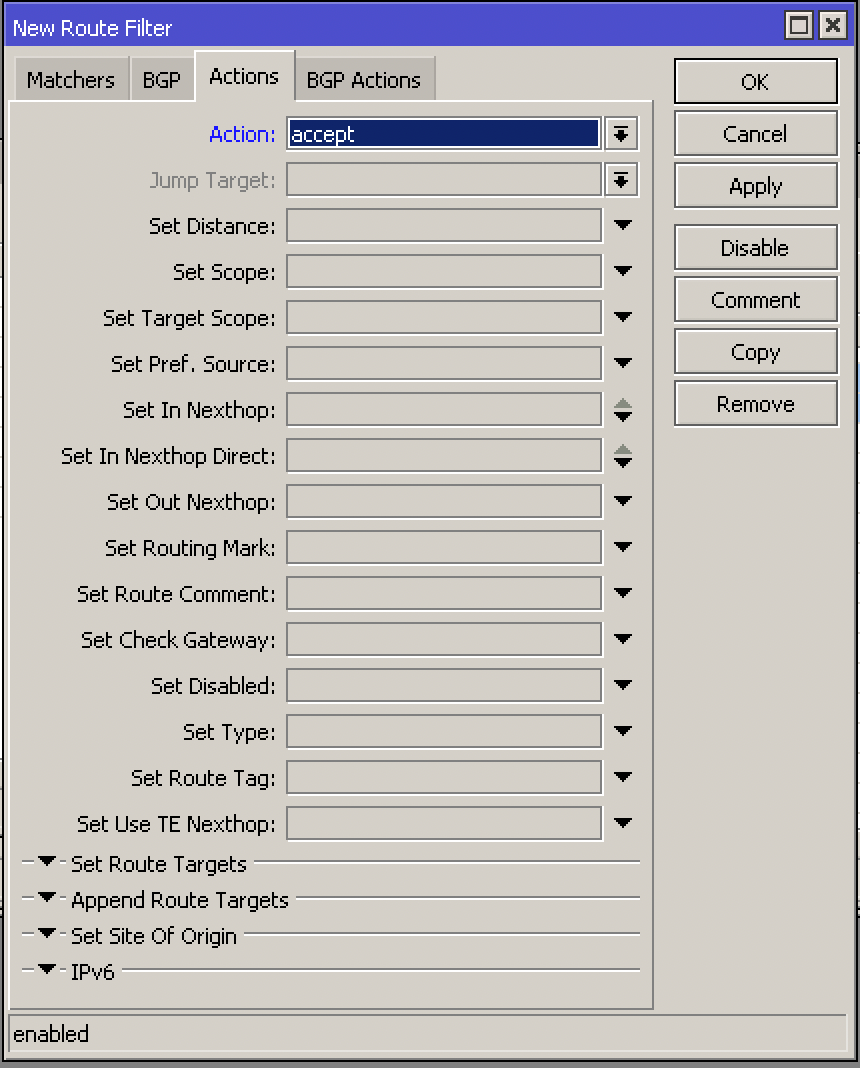
In Actions we will mark it as Accept to accept sending this route
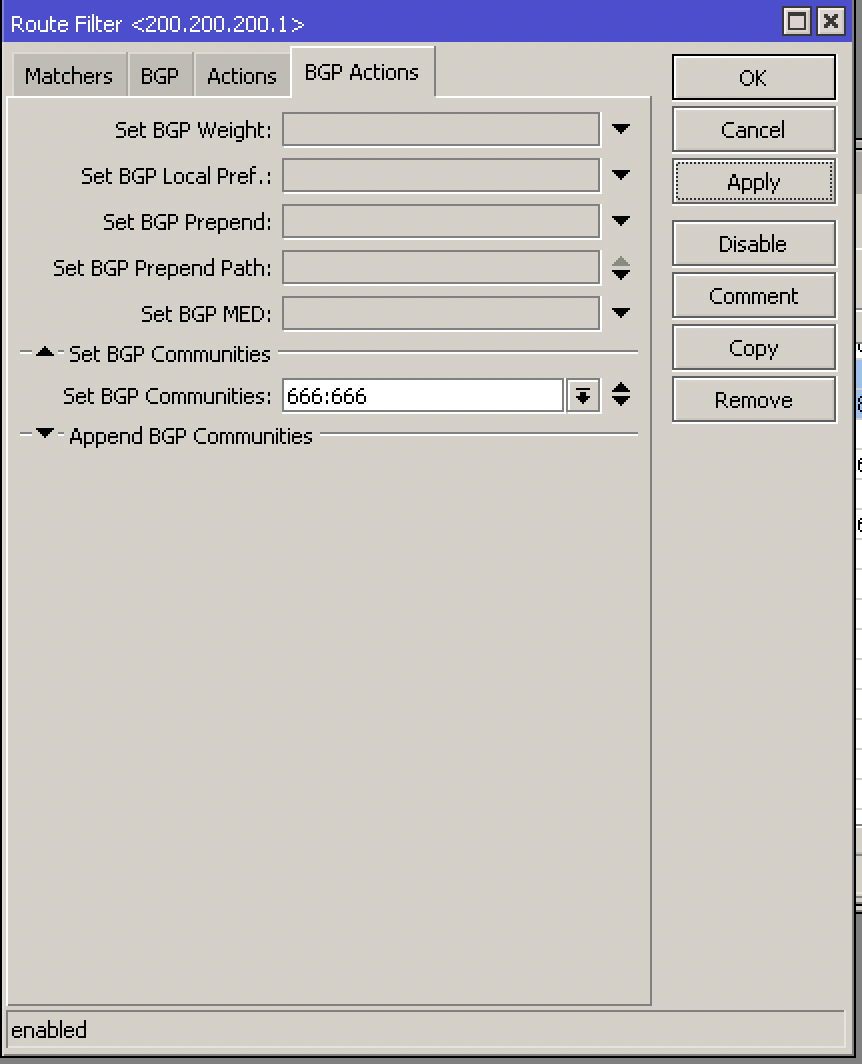
And finally in BGP Actions and add our operator’s community:
Our XPTO carrier uses community BGP 666:666 to send traffic to Blackhole
Via cli it looks like this:
/routing filter
add action=accept chain=TRANSITO-XPTO-OUT prefix=200.200.200.1 set-bgp-communities=666:666
Tip 1: Don’t forget to change the order (Number) of the rule so that it is before the total discard/reject filter. RouterOS reads Filters rules in numeric sequence, from rule 0 onwards.
Tip 2: Talk to your operator to find out which BGP blackhole community they use
Once this is done, the IP will remain in blackhole and announced to your operator, the attack will cease if it goes to this single IP.
To make life easier, we have the video below, showing in practice how to configure the Mikrotik with Blackhole
If you have any doubts, do not hesitate to contact us via WhatsApp, Social Networks or E-mail.
See you next time!


