In our digital age, every day more of our lives are connected to the Internet or World Wide Web. In scenarios like ours in 2021 where the global pandemic has forced many companies to migrate to home-office and fully connected environments, digital crimes or cyber attacks gain strength by the day.
Cyber attacks, are the attacks or cyber crime, which occur within the digital world, over the Internet. Hackers or malicious people attempt to damage, destroy or breach a network or system.
And why these crimes? We can list several as:
- Identity Theft
- Fraud
- Extortion
- scams and other criminal and malicious practices
- Cyberwar or cyberterrorism
- A competitor
And in recent years the amount of cyber attacks has grown a lot, as the news shows:
And cyber attacks are for all kinds of companies, not only for big ones, but also for small and medium-sized ones.
What are they and how do they work?
Cyberattacks come in many shapes and forms. Let’s talk about the main ones, which are:
Backdoor: These are attacks where a door or gateway is created by a virus to control the system, delete or modify files, run programs, or even by the code developers themselves. Imagine the backdoor as a hidden entrance to a fortress. An example of a backdoor is the Trojan Horse
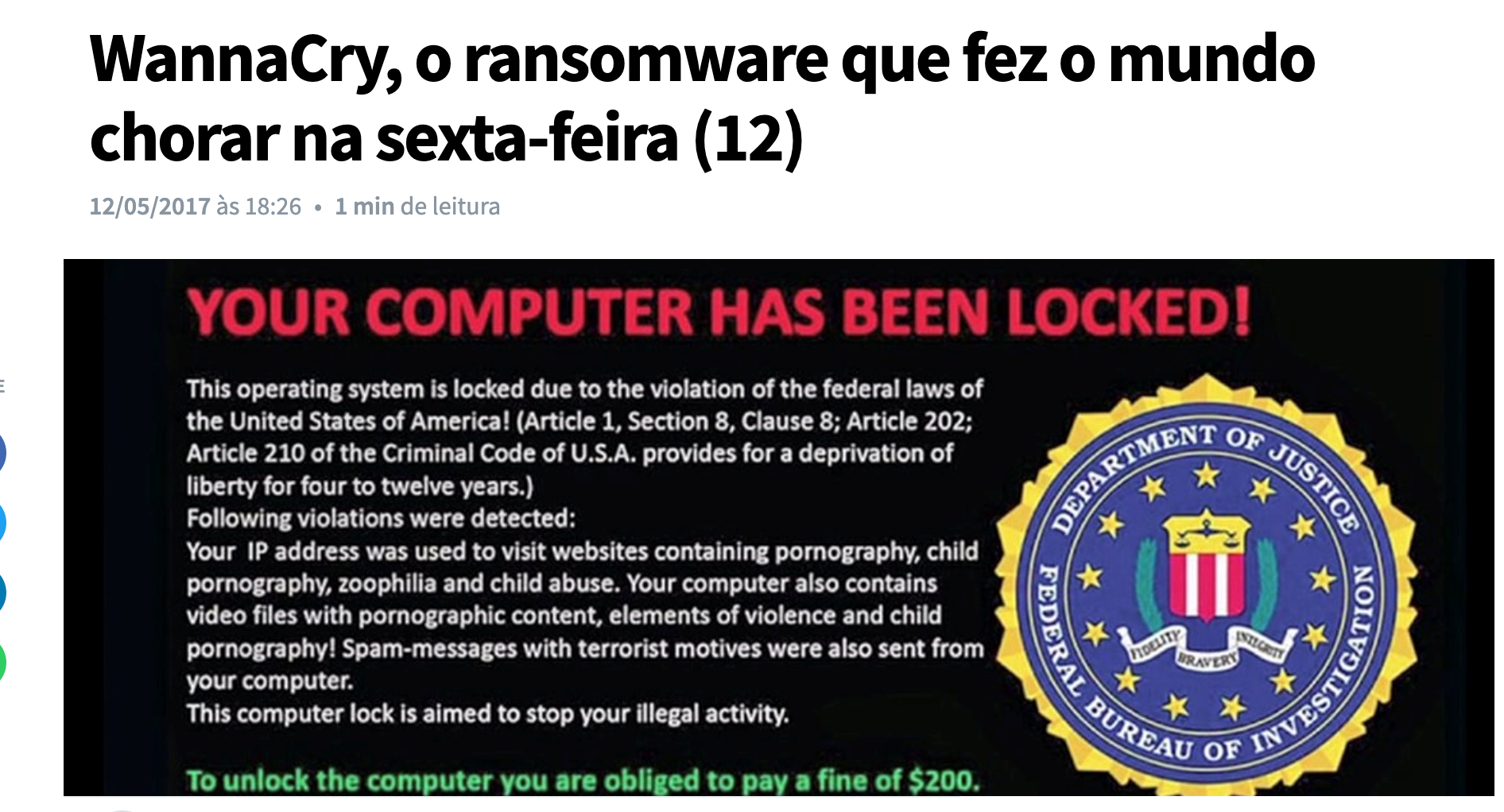
Rasonware: In recent years they have become more famous for infecting many systems around the world. Rasonware is a virus that invades systems and locks files and asks for money (lately bitcoins) to unlock the files. In most cases they affect computers running Windows. Examples of Rasonware are: WannaCry, CryptoLocker and scareware
Phishing: They are very old and still catch many people unaware. Phishing is the attempt to impersonate a person or company in order to trust them to install a virus, access a fake bank site, or pay a fake bill.
Who has never received an email from Itaú, Caixa or Bradesco saying that there is an overdue account? These are one example of phising.
DoS (Denial of Services): These are the famous denial of service attacks. Where his intent is not to steal information or install a virus, but to make a service overloaded and inaccessible. DoS is when a hacker attempts through a computer or server to overload a system or service.
DDoS (Distributed Denial of Services): These are similar to DoS, but the big difference that it is distributed and is executed by thousands and even millions of computers at the same time. Hackers have control of a zombie network (which are remotely controlled infected computers) with millions of hosts and when they want to attack a victim they send commands to each device in the zombie network to attack their victims.
In DDoS we have a few types of attack which are: Volumetric attack, attack to exhaust hardware resources and application layer attack.
As you can see we have several types of cyber attacks existing, and the main question is: Are you and your company prepared for them?
Count on Made4it to increase security in your company!