Overview:
BGP FlowSpec (Border Gateway Protocol Flow Specification) is an extension of the BGP protocol used to define traffic filtering rules on routers. Unlike conventional BGP, which routes based on IPv4/IPv6 and prefix information, BGP FlowSpec allows network administrators to specify more granular criteria for packet forwarding, including layer 4 information (TCP/UDP ports) and even packet patterns.
Flowspec makes it simple for network administrators to create firewall rules dynamically via BGP announcements, using layer 4 criteria such as protocol and application ports and applying actions such as discarding traffic or just applying bandwidth control.
If you want to know more about how FlowSpec works, check out this article explaining whatFlowspec is .
Operation:
BGP FlowSpec works by adding new types of attributes to BGP, allowing network administrators to specify detailed filtering (or dynamic firewall) rules. These rules can include criteria such as:
- IPv4/IPv6 source and destination addresses
- TCP/UDP ports
- ICMP Type
- Protocols
- Bit masks
- Package field values
The following actions can be taken with BGP FlowSpec:
- deny: Blocks the traffic corresponding to the rule.
- rate-limit: Limits the traffic rate corresponding to the rule.
- redirect: Redirects the traffic corresponding to the rule.
- sample: Creates samples of the traffic corresponding to the rule.
- mark: Marks packages matching the rule with a specific mark.
- redirect-to-ip: Redirects the traffic corresponding to the rule to a specific IP address.
- traffic-rate: Limits the traffic rate corresponding to the rule to a specific value.
- traffic-action: Defines action for the corresponding traffic, such as accept, discard or forward.
- redirect-to-blackhole: Silently discards all traffic corresponding to the rule.
When these rules are propagated through the BGP network, routers can use this information to filter or manipulate traffic according to the defined policies,
Operation – More Details:
In the context of BGP FlowSpec, the actions are specified as part of the filter rules. Each filter rule contains three main parts:
- Matching Fields: Specify the matching criteria, such as source and destination IPv4/IPv6 addresses, TCP/UDP ports, protocols, ICMP Type, bit masks and packet field values.
- Action Fields: These specify the actions to be taken for the traffic that corresponds to the rule.
- Protocol Fields: Specify the protocol that the filter rule should apply.
Actions in BGP FlowSpec are coded using BGP communities. Each action is mapped to a specific BGP community:
- The deny action can be represented by a specific BGP community, such as 65535:666.
- The rate-limit action can be represented by another specific BGP community, such as 65535:777.
- The redirect action can be represented by a different BGP community, such as 65535:888.
When you create a BGP FlowSpec rule, you specify the matching fields, the desired action and, optionally, protocol fields. This rule is then encoded as a BGP community and included in a BGP update message that is sent to neighboring routers. The routers that receive this rule apply the specified actions to the packets that match the matching criteria.
Please note that the specific BGP communities for each action may vary depending on the BGP FlowSpec implementation on your router. I recommend consulting your equipment’s documentation for detailed information on the BGP communities associated with each action in BGP FlowSpec.
Use Cases:
- Mitigation of DDoS attacks:
BGP FlowSpec can be used to block or redirect malicious traffic during distributed denial of service (DDoS) attacks. Precise rules can be applied to filter out unwanted traffic and keep services online.
- QoS (Quality of Service) policies:
Network administrators can use BGP FlowSpec to guarantee quality of service by prioritizing certain types of traffic based on specific ports or protocols.
- Implementation of security policies:
BGP FlowSpec can be used to implement granular security policies, blocking traffic associated with malware or suspicious activity.
Configuration examples:
Now that you know what FlowSpec is and what it can do, we’re going to show you how to configure FlowSpec on Huawei routers. This configuration applies to Huawei NE20, Huawei NE40, Huawei NE8000-M4, Huawei NE8000-M8, Huawei NE8000-M12, Huawei NE8000-F1A or any Huawei that uses Huawei’s VRP operating system.
Example configuration of the dynamic BGP flow specification:
If the characteristics of DoS or DDoS attack traffic are unknown, a traffic analysis server, such as Made4Flow with Anti-DDoS, can help implement the BGP flow specification to ensure network security.
#Network requirements:
As shown in the Topology below, Device A belongs to AS 100, while Device B, Device C and the Server belong to AS 200. Device B is an input of the AS 200. AS 200 communicates with AS 100 via Device B.
The source of the attack in AS 100 can flow to AS 200 via Device B, posing a threat to AS 200. In this situation, configure dynamic BGP flow specification to ensure network security. The operating process is as follows:
- Deploy a traffic analysis server such as Made4Flow with Anti-DDoS;
- and establish a FlowSpec BGP session between the Traffic Analysis Server Made4Flow and device B.
- Device B collects traffic samples periodically and sends the traffic sample to the Made4Flow .
- O Made4Flow generates a FlowSpec BGP route based on the characteristics of the sampled attack traffic;
- and sends the route to device B.
- Device B converts the route into a traffic policy (such as a firewall rule) to filter and control attack traffic, ensuring the proper transition of services in AS 200.
Note: Interfaces 1 to 3 in this example represent GE 1/0/0, GE 2/0/0 and GE 3/0/0 respectively.

The configuration script goes as follows:
- Configure an IP address for each interface.
- Establish a BGP FlowSpec session between device B and Made4Flow to allow the generated BGP FlowSpec routes to be sent to device B. A traffic policy is then generated.
Data preparation:
To complete the configuration, you need the following data:
- Device A’s router ID (1.1.1.1) and device B’s router ID (2.2.2.2).
- AS number of Device A (100) and AS number of Device B, Device C and Made4Flow (Server) (200).
Procedure:
- Configure an IP address for each interface.
- For detailed settings, see the configuration files in this example (below).
- Set up a BGP Flowspec peer and disable route authentication.
We are going to demonstrate the commands used, in our laboratory we are using a simulator such as PNETLAB/EVE-NG.
#Configuredevice B:
[~DeviceB] bgp 200
[*DeviceB-bgp] peer 10.2.1.2 as-number 200
[*DeviceB-bgp] ipv4-family flow
[*DeviceB-bgp-af-ipv4-flow] peer 10.2.1.2 enable
[*DeviceB-bgp-af-ipv4-flow] peer 10.2.1.2 validation-disable
[*DeviceB-bgp-af-ipv4-flow] commit
[~DeviceB-bgp-af-ipv4-flow] quit
[~DeviceB-bgp] quit #Checkthe peer connection status of the FlowSpec session on device B, if the session has the status “Established” the session is correct and functional.
<DeviceB> display bgp flow peer
BGP local router ID : 2.2.2.2
Local AS number : 200
Total number of peers : 1 Peers in established state : 1
Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv
10.2.1.2 4 200 9 10 0 00:00:35 Established 1 #Checkthe routes received via BGP Flowspec by device B:
<DeviceB> display bgp flow routing-table
BGP Local router ID is 2.2.2.2
Status codes: * - valid, > - best, d - damped, x - best external, a - add path,
h - history, i - internal, s - suppressed, S - Stale
Origin : i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V - valid, I - invalid, N - not-found
Total Number of Routes: 1
* > ReIndex : 97
Dissemination Rules:
FragmentType : match (Don't fragment)
MED : 0 PrefVal : 0
LocalPref: 100
Path/Ogn : i#Checkthe traffic policy (Dynamic firewall rule) on each BGP Flowspec route based on the ReIndex shown in the previous output:
<DeviceB> display bgp flow routing-table 97
BGP local router ID : 2.2.2.2
Local AS number : 200
ReIndex : 97
Order : 2147483647
Dissemination Rules :
FragmentType : match (Don't fragment)
BGP flow-ipv4 routing table entry information of 97:
Match action :
apply deny
From: 10.2.1.2 (10.2.1.2)
Route Duration: 0d00h02m26s
AS-path Nil, origin igp, MED 0, localpref 100, pref-val 0, internal, pre 255
Not advertised to any peers yetComplete scenario configuration files:
Device configuration file A:
#
sysname DeviceA
#
interface GigabitEthernet0/1/0
undo shutdown
ip address 10.10.1.1 255.255.255.0
#
bgp 100
peer 10.10.1.2 as-number 200
#
ipv4-family unicast
undo synchronization
peer 10.10.1.2 enable
#
return Device configuration file B:
#
sysname DeviceB
#
interface GigabitEthernet0/1/0
undo shutdown
ip address 10.10.1.2 255.255.255.0
#
interface GigabitEthernet0/2/0
undo shutdown
ip address 10.2.1.1 255.255.255.0
#
interface GigabitEthernet0/3/0
undo shutdown
ip address 10.1.1.1 255.255.255.0
#
interface LoopBack1
ip address 2.2.2.2 255.255.255.255
#
bgp 200
peer 10.2.1.2 as-number 200
peer 10.10.1.1 as-number 100
#
ipv4-family unicast
undo synchronization
peer 10.2.1.2 enable
peer 10.10.1.1 enable
#
ipv4-family flow
peer 10.2.1.2 enable
peer 10.2.1.2 validation-disable
#
return
- - - Below is another basic example of a BGP FlowSpec rule to block traffic from a particular port:
Validate BGP Flowspec routes received:
display bgp flow routing-table 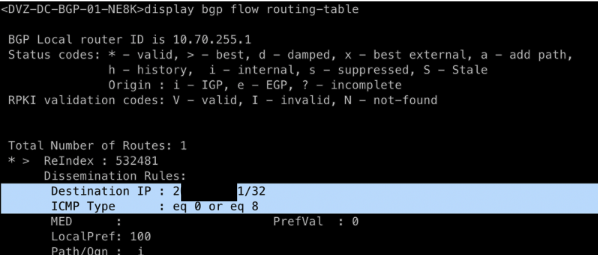
Validate details of the route received:
display bgp flow routing-table 532481 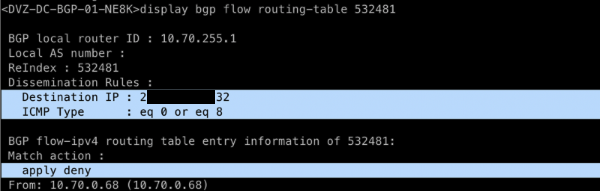
To check whether the BGP Flowspec routes are effective, you can use the commands below:
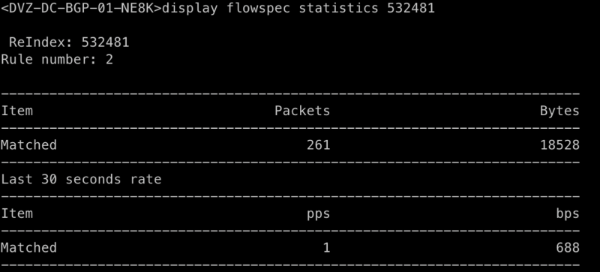
Validate route statistics:
display flowspec statistics $REINDEX
system-view
diagnose
display fe slot 9 fe-id 0 table flowspec action $REINDEX More commands for validations:
system-view
diagnose
display fe slot 9 fe-id 1 table flowspec action $REINDEX
display fe slot 9 fe-id 1 table flowspec relation $REINDEX
display fe slot 9 fe-id 1 table flowspec rule $REINDEX Example of a Flowspec route with rate-limit:

RFCs:
For detailed information on BGP FlowSpec, see the following RFCs:
- RFC Editor
The RFC Editor is the official resource for RFCs (Request for Comments) that define Internet standards, including BGP FlowSpec. - RFC 8955: Dissemination of Flow Specification Rules
This RFC describes the flow specification rules in the context of BGP FlowSpec. - RFC 8956: Dissemination of Flow Specification Rules for IPv6
This RFC extends BGP FlowSpec support to IPv6, allowing the specification of flow rules for IPv6 traffic.
Be sure to consult these RFCs for detailed information on BGP FlowSpec and its extensions.
Did you know that Made4Flow now has automated BGP Flowspec in its configurations and you can protect your network and your customers using this technology?

You can automate BGP FlowSpec announcements with discard, rate limit and flexible rules.