Hello everyone!
In our last article we learned how to install and configure PFSense, to be used as the Gateway of your network, allowing it to act with several functionalities for the network. Today we will introduce you to creating a VPN with OpenVPN, so you can access your entire internal infrastructure from anywhere you need to.
What is a VPN?
Basically, VPN stands for Virtual Private Network, and it serves as a tunnel between two connection points.
By establishing a VPN between a computer at home and a PFSense in your company, for example, the tunnel created makes your computer act as if it were ‘inside’ your company’s local network, allowing access to servers and equipment, if PFSense is reachable from your home machine.
Now that we understand what VPN is all about, let’s learn how to set it up using PFSense to establish the connection between your different networks.
Configuring the VPN
We will use the PFSense Wizard for this configuration. To do this, we go in the menu VPN > OpenVPN . Then, click the Wizards tab :
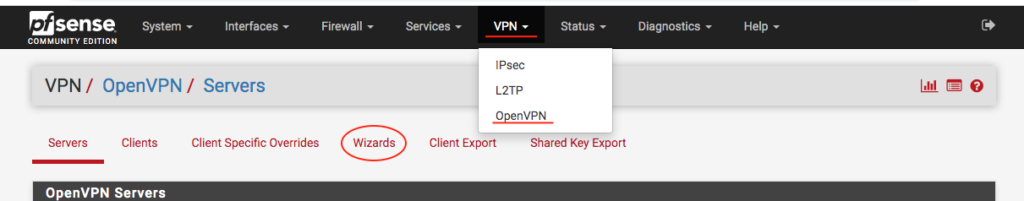
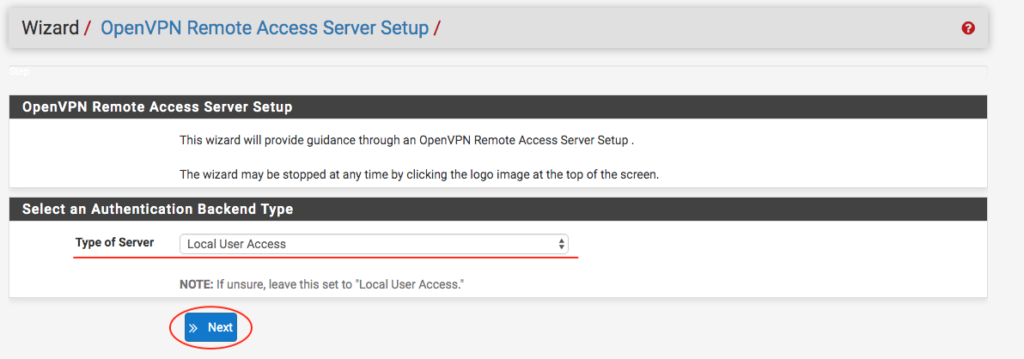
When we access the Wizard, we will select the‘Type of Server‘, as‘Local User Access‘, and we can click on ‘ Next ‘.
On the next screen you need to create a new Certificate Authority (Cerfificate Authority, or CA), by filling out the following fields:
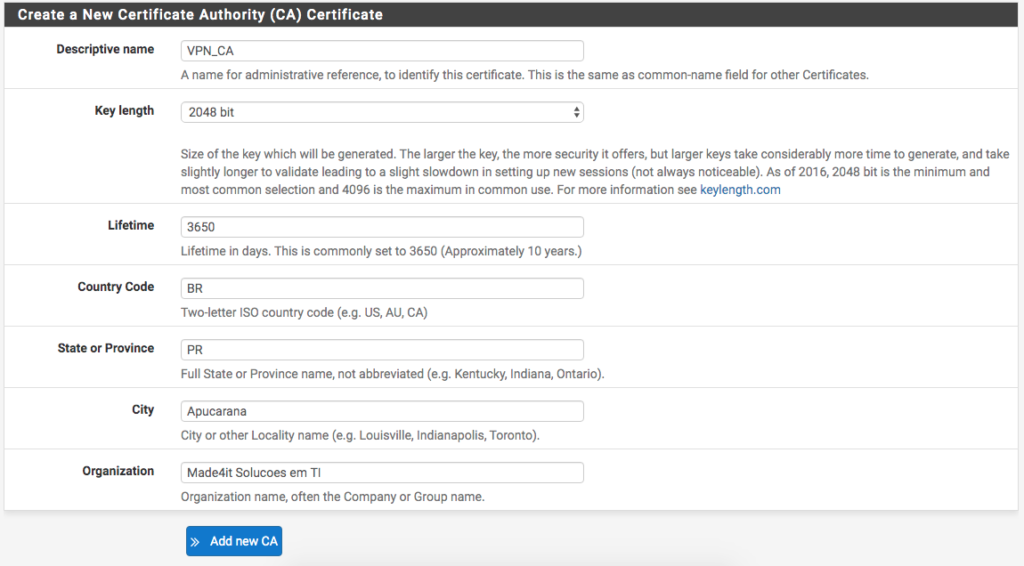
We will use the name:
VPN_CA
to indicate that this CA is used for the VPN. After that we are entering the size of the encryption key that will be generated. A value of
2048
bit value is sufficient.
The rest can be filled in according to your data of
Country, State, City and Organization
(or company).
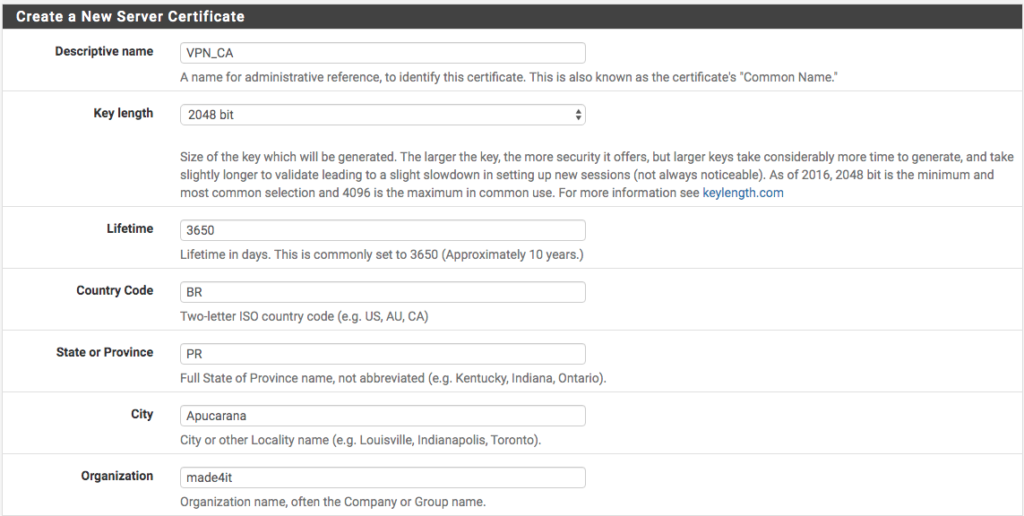
Finishing up the Server Certificate, let’s make the settings for accessing the VPN itself. To do this, we choose the access interface, in our case the WAN . Then we fill in the rest of the data. I will use the UDP only on port 1194 and with the description ‘ VPN ‘.
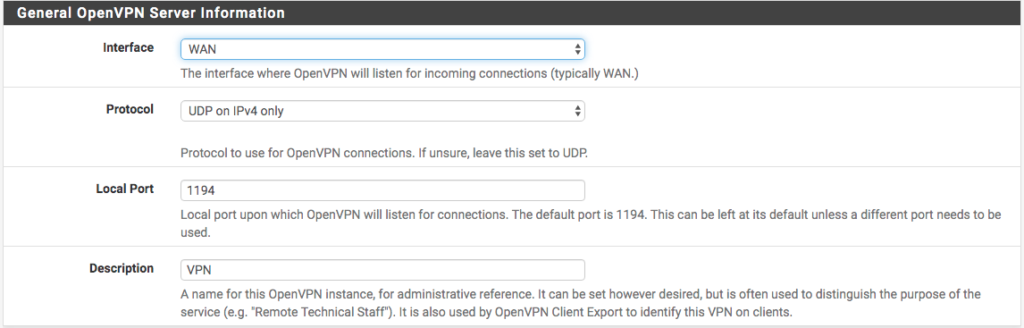
Following on the same screen are the encryption settings. In these options, we will leave
enable TLS authentication and the automatic creation of a shared TLS key for authentication.
.
We can define the ‘
DH
with a value of
2048
as the default, and change the
Encryption Algorithm
to
AES-256-CBC
. Let’s choose the
SHA1 (160bit)’ authentication algorithm
. It is important that this option is the same on the Server side (PFSense) as on the Client side (your machine).
We have our configurations as follows:
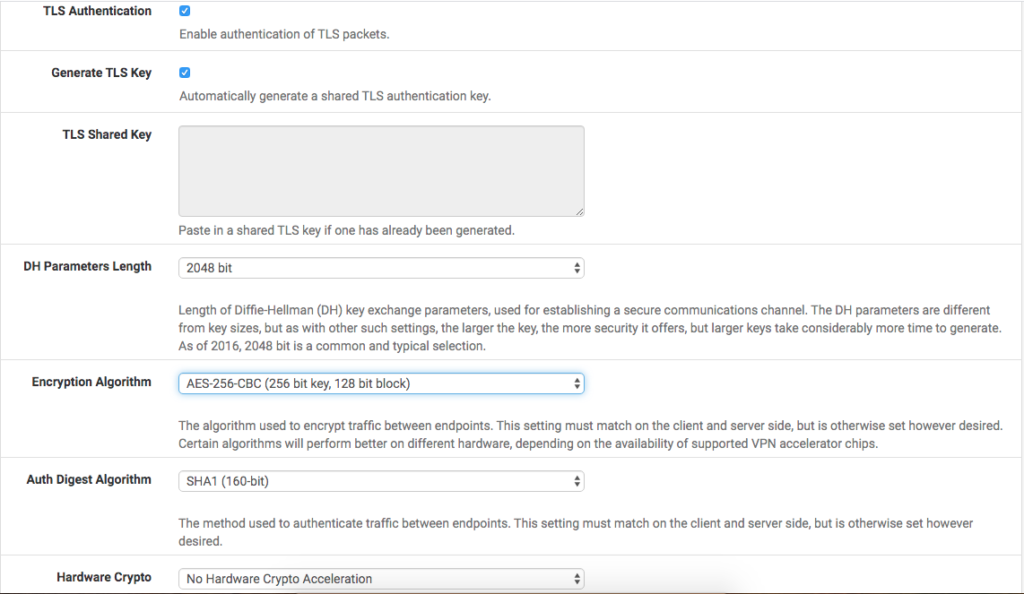
In the next part we have the Tunnel settings.
The first field refers to the IP pool that PFSense will use for its Clients, that is, which IPs the PCs that connect to the VPN will receive for the Virtual Network. In our case, we select a /24 block (256 IPs, 254 hosts), which is a good size. We take the block
10.20.50.0/24
.
We will fill in the option ‘
Local Network
to indicate the LAN network we are trying to access so that PFSense can automatically create a route to this network. In our example, the network is
192.168.1.0/24
.
We use the compression ‘
Omit Preference
compression, and enabled the ‘
Inter-Client Communication
if you want the machines connected to the VPN to communicate with each other.
At the moment, our settings are as follows:
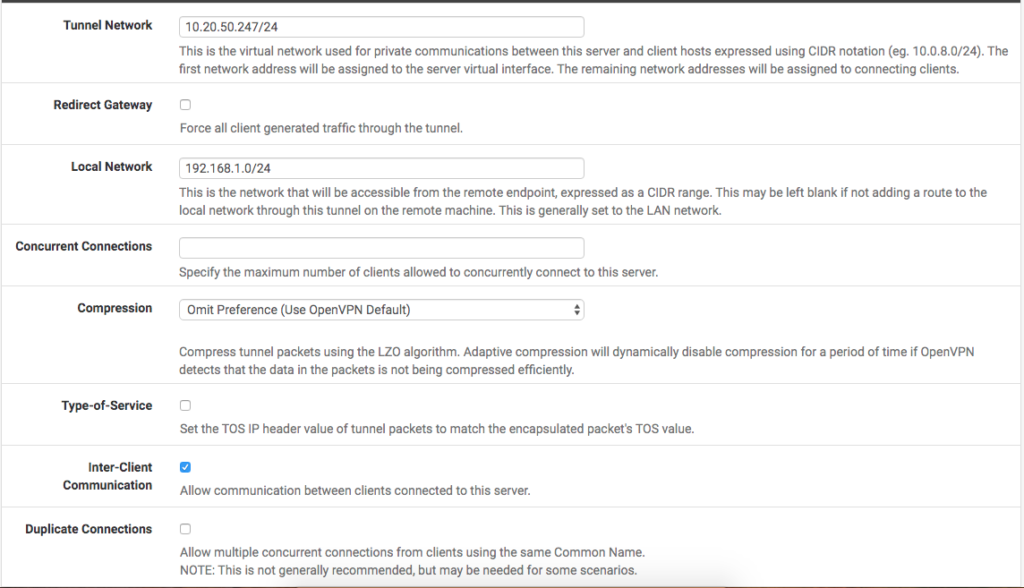
To finish the configuration, in the ‘
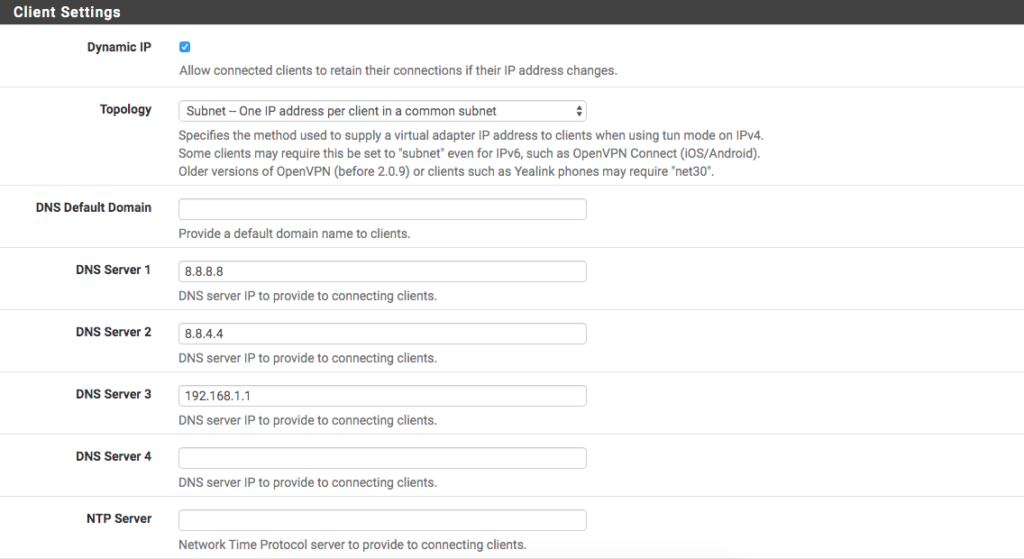
Client Settings
field, we have the option
Dynamic IP enabled
to have dynamic IPs connected. At
Topology
we select the option
Subnet
to have a /24 with the IPs distributed within the block. If you want to isolate the subnet of each client, we have the net30 option, in which each client will have a separate /30. Some older versions of Clients require it to be marked in net30, while others require it to be marked in Subnet. It is important to adapt your configuration to the Client that will be used.
After that we have the option to choose the DNS server for this VPN connection. Let’s leave the pattern
quad-8
pattern and PFSense itself as DNS Servers.
The final settings are as shown in the picture:
On the next screen, we have the option to set a Firewall rule to allow connections from anywhere in the VPN, which we can enableOpenVPN uses certificates to connect, and without the certificate (which must be passed directly to the person connecting) and user/password, it is impossible to gain access to this network.
Just below it, the option ‘
OpenVPN rule
option, we can
enable
to allow all traffic from connected clients to pass through the VPN Tunnel.
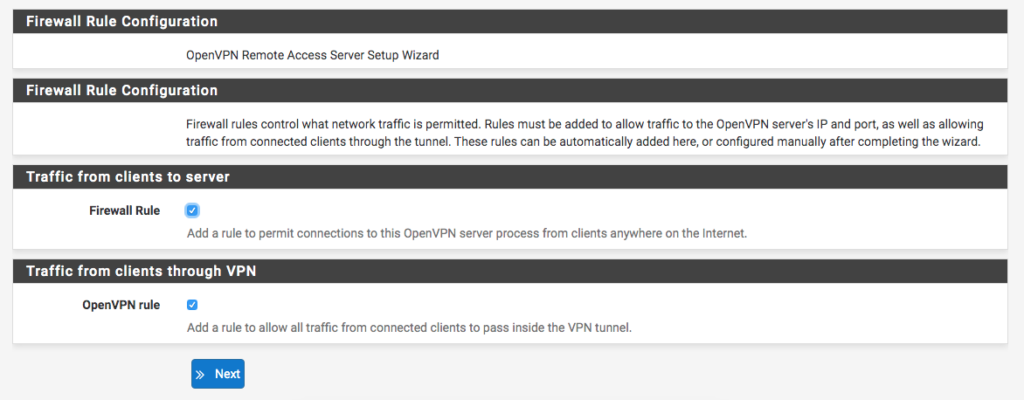
Finally, we finish the configuration and have the VPN ready.
Now we need to create the users that will have access to the tunnel.
Creating user with certificate for VPN
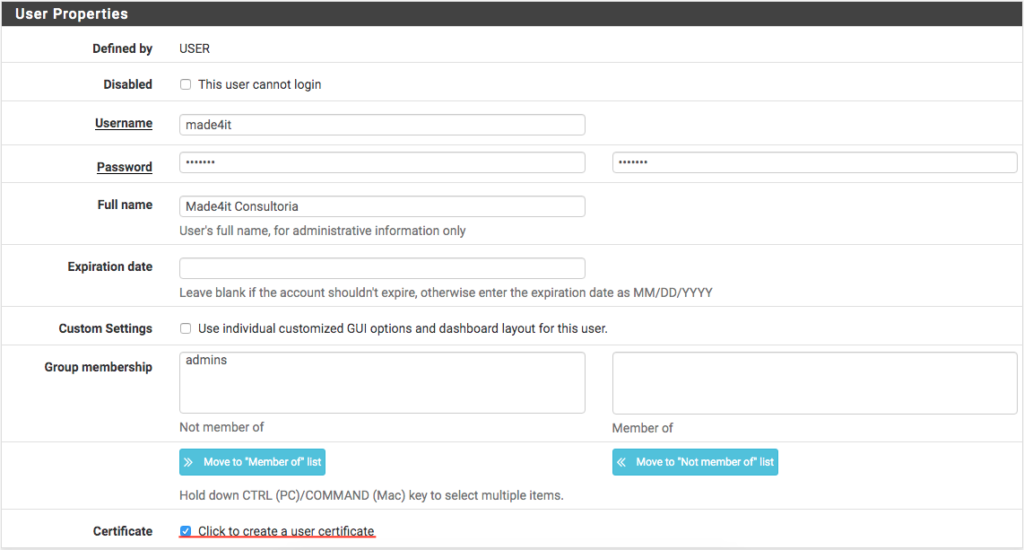
To create our users, go to System > User Manager and then go to ‘ + Add just below the panel with your PFSense users.

In user creation, we add User , Password and fill in the rest with the user’s data. In this case, I will create a user ‘ made4it which we will use to connect to the network.
Below the group selection we have a ‘ button Certificate ‘. You must give a check on it to create the user certificates.
Below the user settings we will create the certificate for our user. To do this, we create a description. Let’s use ‘ made4it_cert in our example. We select the CA created earlier and specify the same 2048 bits that we used to create it.
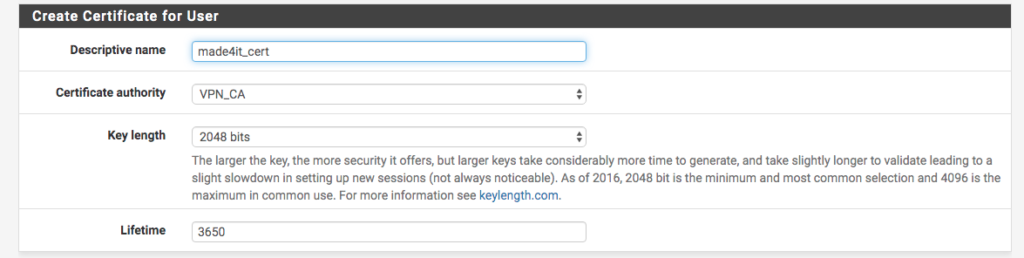
Once this is done, we can save our user.
To access the VPN, we need to export our certificate, using the package ‘
OpenVPN Client Export
‘.
Client Export Installation
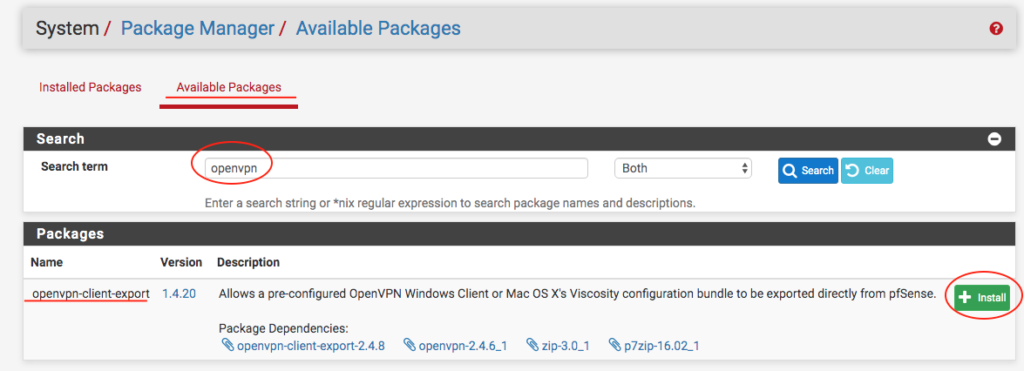
Let’s go to System > Package Manager > Available Packages and then, search for the package ‘ openvpn-client-export and give it a ‘ + Install on it, then wait for the installation to finish:
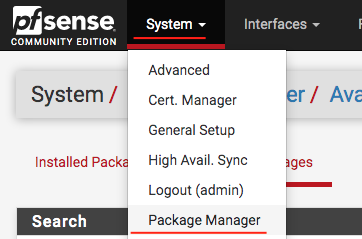
Once the installation is complete, simply access
VPN
>
OpenVPN
>
Client Export Utility
to start exporting the certificate.
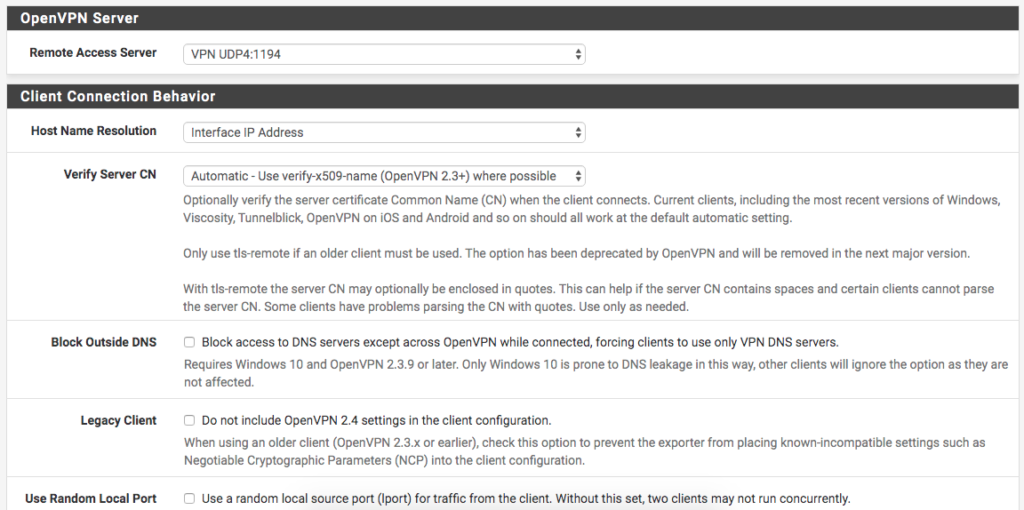
On this Screen, we will leave the option ‘
Host Name Resolution
‘ as ‘
Interface IP Address
‘. In ‘
Verify Server CN
we can leave it at ‘
Automatic
‘.
The rest can be left unchecked, so we click on ‘ Save as Default to apply the changes.
With the changes applied, we go to the bottom of the screen, to the user we created, and select the certificate/client that we will export.
In my specific case, I will download the ‘ Most Clients ‘ into ‘ Inline Configurations because I already have a client ready. If you are going to use a Windows client, Viscosity (Windows or MacOS), or another client, just choose the file accordingly.
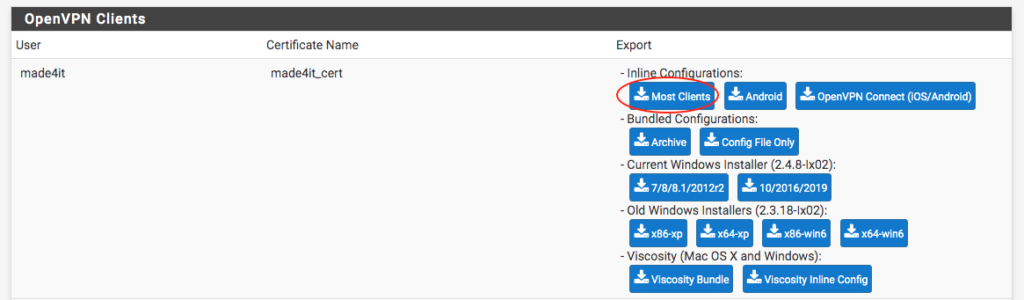
In my case, I will use the Client ‘. Tunnelblick client on MacOS to connect to the VPN. To make the connection, simply add the configuration files to your client, then when connecting you will be prompted for the VPN user and password, which will be from the user you created earlier, in our case, the user ‘ made4it ‘:
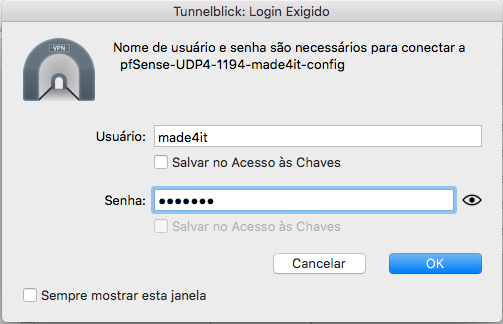
Setting up VPN in Windows
To connect to our VPN already configured on Windows, we need a Client. We can install the OpenVPN Client using the files that PFSense itself makes available to us.
To do this, we go to
VPN > OpenVPN > Client Export
and download the most suitable file. In this case, as I will be using the OpenVPN Client, we can select the version in
Current Windows Installer
(For Windows 7/8 or Windows 10).
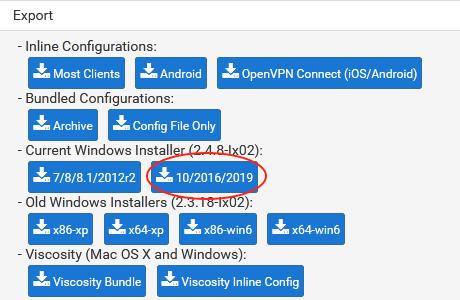
Once the file is downloaded, we can run it and proceed with the normal installation. The File we downloaded will start the OpenVPN configuration and install our VPN connection directly, with no further configuration required.
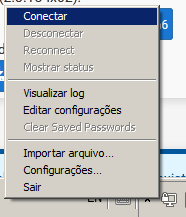
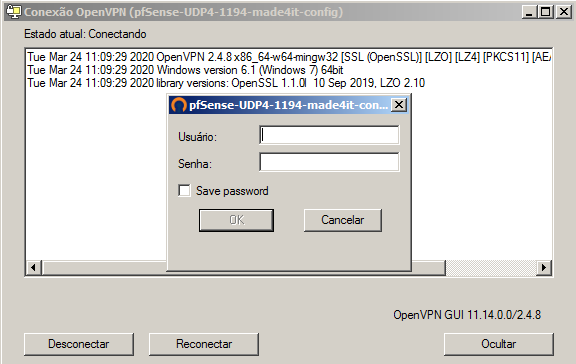
When the installers are finished, we can open OpenVPN by clicking on the shortcut created on the desktop, then right-click on the icon in the Toolbar (Next to the Clock), and finally click Connect and provide the user/password data created in PFSense.
So that’s it folks, this was our guide to setting up OpenVPN using PFSense and configuring how to connect to it using the OpenVPN Client, with the files provided by PFSense itself.
Thanks and see you next time!

